- Print
- DarkLight
The cloud scanner is responsible for scanning cloud configurations from main 3 providers: AWS, Azure and GCP. The scan includes services that are part of the best practices named in the CIS benchmark documents.
The cloud scanner requires a credential with enough permissions to review required configuration information. This permissions are mostly viewer or audit, but there might be also some others that require a higher level due to particularities of the providers in the information that they deliver with the different levels of access.
The main steps of the Cloud Scanner are the following:
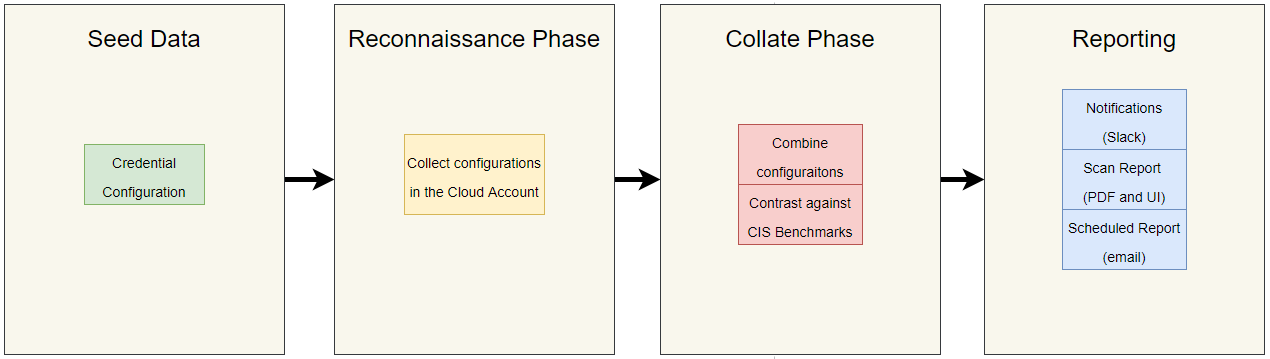
As shown in the image above users only have to supply the initial seed data and the tool will automate the rest of the process. The platform is designed collect configuration information of all of the services present in the CIS Benchmark associated to the cloud provider of use. The information collected does NOT include any sensitive data, it is merely configurations about the services, but NOT data processed in those services.
Finally, after a scan has completed you can download a scan report of the vulnerabilities present in the analized account. This report can also be scheduled to be sent periodically (in configurable periods) to provided list of emails. In addition to reports you can also get notified when a new vulnerability is found by integrating into slack and other third party tools.
In order to see all of the sentries available to the loged account in current team, en the left menu panel, the 'Sentries' option has to be clicked, and then the tab 'Cloud', as the following picture shows.
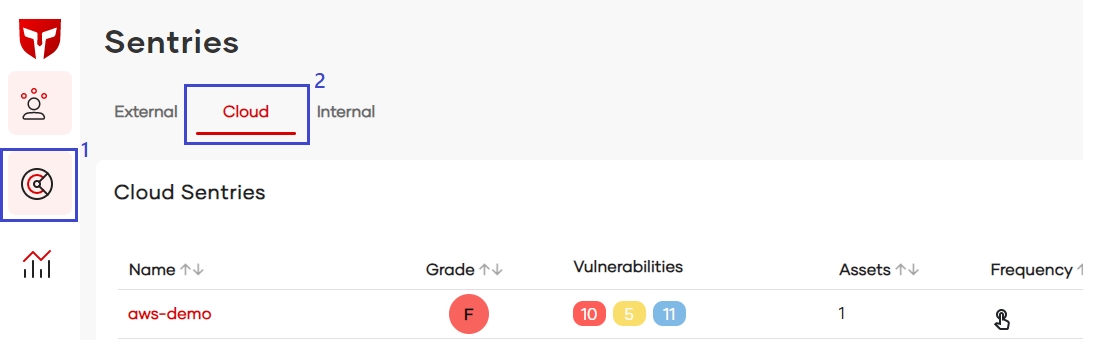
To find out how to configure a Cloud Sentry, please go to Onboarding section.
.svg)
